
Using AI in cyber security
May 4, 2023Password Security
How passwords and security improves your defence against cyber crime?
Passwords are the first line of defence when it comes to securing your online accounts. To maximize its potential, it has to be used the right way.
These are the biggest mistakes you can do handling your password:
- Using short simple logical words and/or sequential numbers (abc123, printing123, AdamPage)
- Re-using the same password everywhere
- Printing out and leaving passwords in a visible area (desktop, sticky note on your desk)
- Never changing your password
How basic password authentication works?
In a best practice scenario, passwords are stored in hashes. Hashes are derivatives of a (mostly) irreversible/one-way mathematical function. In other words, when you are registering into a new website and type in the password, your clear text password will go through a mathematical function which will produce a password hash as a result.
For example, your password is:
“Hello*Word12$”
Hashing this password with a hash function called sha256 will produce this hash:
“01c0e5ec258ec279e7611b0e53a8c26ec57fb7ebf7d3ce6e1d4a1d3df66246e4”
This is actually what’s stored in the database of the website you are logging in to, and not your actual text password of “Hello*World12$”
Next time you log in to the same account, the same function will be applied to your password and if the resulting hash matches the one in the database, you will be granted to log in. If the result doesn’t match, you will be denied to log in – of course. The only reason the hash wouldn’t match if you put the wrong password in.
What if a hacker steals my hash from the website?
First of all, they wouldn’t be able to use the hash to log in to the web platform. If the hacker puts the hash into the password field, the hash will be hashed before it gets compared to the database, which again will be a mismatch and wouldn’t grant the login.
Can they do anything with the hash?
Short answer is, the hash can still be useful to them. The hacker knows the result of the equation and they can guess what algorithm was used by looking at the length of the hash.
Example of an extremely simplified version of your password mechanism:
YourClearTextPassword > Irreversible Hashing Algorithm = PasswordHash
Now the hacker can try to figure out what they can put into the “YourClearTextPassword” so they can get the “PasswordHash” field. In other words, if they try guessing “password123” and they put it through the hashing algorithm, the resulting hash is the same as the stolen hash. They will know that “password123” was your clear text password.
In this scenario we can say your password is cracked. Now the hacker will try loads of inputs into the “YourClearTextPassword” field, until they get the same hash as the stolen one. If your password is more complicated [alhpanumerical+special characters] the “guessing” is really hard.
Some common methods the hacker would try to hack your password?
Dictionary: Typically they will use a dictionary first, a compilation of most used passwords which they will run one by one through the hashing algorithm until it finds a match. If your password is really “password123” it will probably be on that list and your password will be cracked in seconds.
Brute force: If you password was a bit more random like “UtJX04%RDJ0UE*xd” it will definitely not be on the most common passwords list and they will be forced to use a different method, called brute forcing. This would include checking every possible character combination to try and crack your password.
Rainbow Table: Explaining rainbow tables in depth should be a completely new blog post itself. To explain it in simple terms, rainbow tables are a set of pre-calculated sets of passwords and hashes.

Things that help the hackers
Let’s say your password only can have the lower case characters of the alphabet and your password length can only be a minimum length of 3 and a maximum length of 5. This information is obtained by trying to log into the questionable website.
Brute forcing would look like this:
It would start with aaa,aab,aac,aad,aae…. and will end with zzzzv,zzzzw,zzzzx,zzzzy,zzzzz
(This is 12355928 possible passwords)
Is this the same as going to a website for example and just trying to guess the credentials to log in and physically type in the passwords?
YES and NO. Most web services have a rate limiting implemented, which means that most likely your IP address will be banned from that service for a set amount of time, or even forever. Also just typing in a few million combinations even with a purpose built app is just going to take forever.
However, if the hacker knows the hash and the algorithm used, they can start “guessing” the password within their own system without ever interacting with the web service and depending on the hardware used. This can be blazingly fast.
Time to guess passwords
The average time to guess the example above (lowercase alphabet with maximum of 5 characters ) resulting 12355928 possible combinations, passwords would take less than a second to find. This is why using a proper password is so important.
To make it harder to guess the password we have to implement more possible combinations to the scenario. First of all the website we are using needs to allow lowercase characters, uppercase characters, numbers and special characters.
A few more time calculations for password cracking:
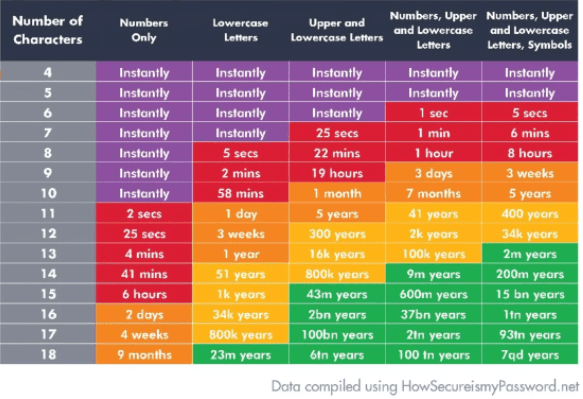
As you can see, nothing is really uncrackable but it takes time and computing power. Our goal is to make it hard enough, so it’s not worth doing it. It is possible to build a supercomputer to crack passwords extremely fast. Japan’s Fugaku supercomputer would probably break the hardest passwords much faster, but it will cost a whopping 1 billion dollars to build one. Guessing your facebook password with Fugaku is probably not the most economically sane project for any evil hacker.
So what is a good password?
A good password has a minimum of 10 characters, uppercase, lowercase, at least 3 numbers and at least 2 characters. Most websites and apps accept this combination but if you can, make it even longer.
How can I memorize long passwords?
Try to use a word obvious to you only, then add a combination of symbols and numbers. Using character replacement like 3n3rg!$er is still good (48 years to crack*). However the dictionaries will predict the symbolic use of the character replacement, so while it’s not bad it’s still not the best approach. It’s even better if you use the special characters and numbers after or before the memorable world. While this is less memorable than the first one, it makes the password way longer to crack.
Energizer33!$
(152 million years to crack* as of 2022)
How can you memorize such a complicated password?
You don’t have to. There are loads of password managers out there that can handle your complicated passwords. These are storing your passwords under a master password, bundled with some more sophisticated server side security, to protect your passwords and multi factor authentication.
1password for example uses a browser extension as well. Once you logged in with your master password, it fills in the password field everywhere you have already logged in before and saves your credential in 1password. With this, you can have really long and complicated passwords for each website you are logging in.

Hardening your security
For more sensitive accounts including 1password itself, always use two-factor(2FA) authentication for the login. After putting in your user name and password, the service will challenge you with a second authentication which is unique to you. A memorable word or a sequence of numbers sent to you by text or generated by an app that is synchronized with their service.
One of the safer options for a two-factor authentication is using google authenticator. Most services that offer 2FA will work with google’s authenticator app. This works by generating a 6 number sequence on an app, which changes every minute. The service you are trying to log in is generating the same sequence unique to you. When they match, the service knows it’s you and lets you in.
An even safer option is to use a hardware key like Yubikey, Google Titan and others.
Lastly, don’t use the same password everywhere. Not all web services are taking security seriously. A badly managed web service could store your password in clear text. Unfortunately, we know a few large companies with millions of users that do this even today. If this gets compromised or your password hash gets cracked, all your other accounts using the same password will get compromised soon.
It’s a common technique amongst cyber criminals to try something named credential stuffing. This means if they have one credential (user, password) from you, they will try to log in with these into other services as well, and if you use the same password, they are IN!


